Log the requests
Situation
The Juice Shop is growing rapidly. Great work! Now that you have a set of rules, it is becoming more difficult to reason which rule is responsible for blocking a request. It would be helpful to have some logs. To do this, you need to enable logging for your Web ACL to an S3 Bucket. Your logs contain a sensitive header, named Cookie. You don’t want this to be stored in your logs. You will need configure the redaction of this header in the logs.
Log the requests
WAF Uses Amazon Kinesis Firehose to ingest logs. This allows logs to be passed to any Kinesis Firehose destination, such as Amazon S3, Amazon Redshift or Amazon Elastic Search. To enable logging of requests in your Web ACL, you must first create a Kinesis Data Firehose.
- Go to Amazon Kinesis Console.
- Click Kinesis Data Firehose.
- Click Create delivery stream.
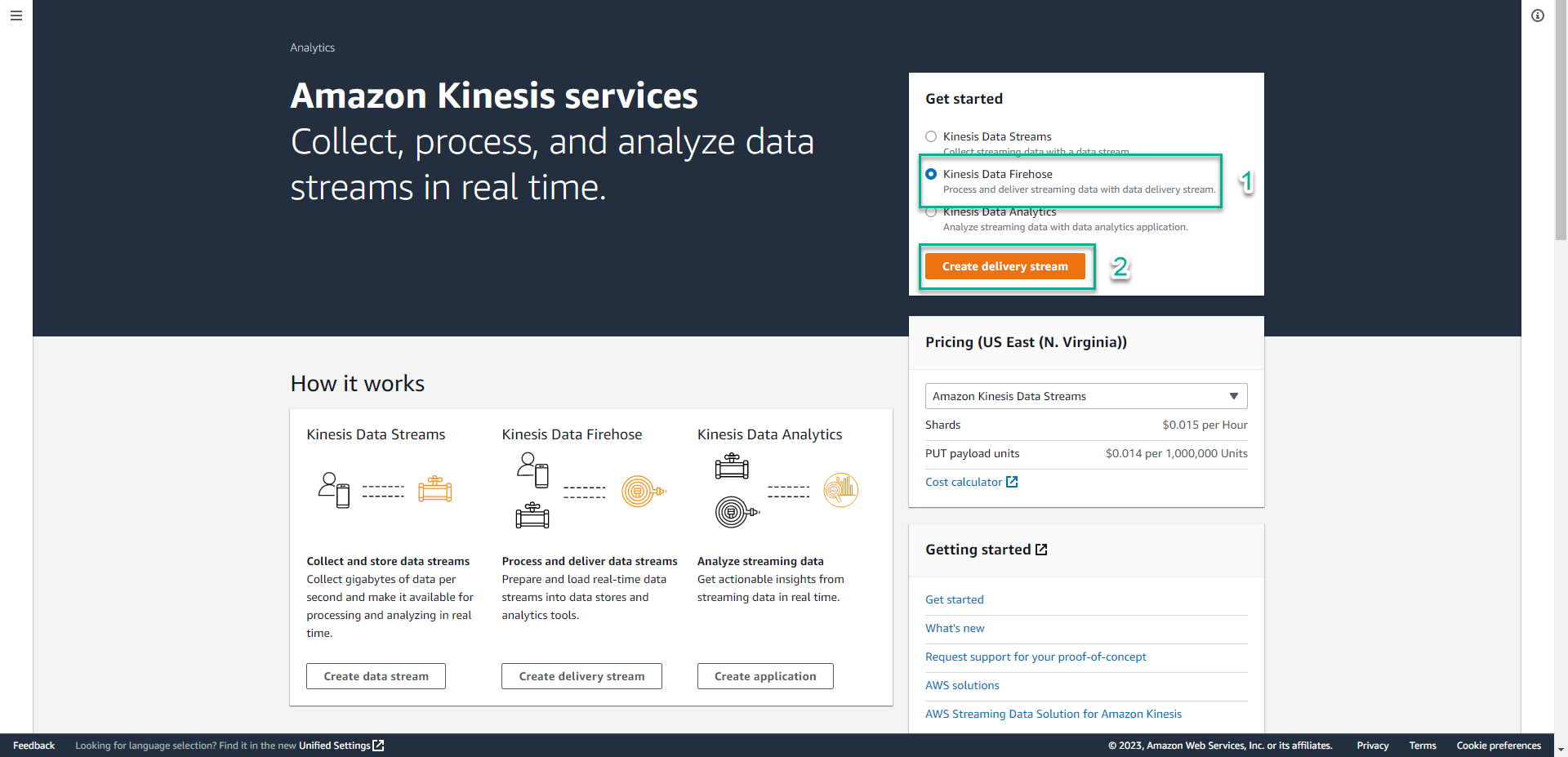
Make sure to create the resource in us-east-1. [This is required when capturing logs for CloudFront](https://docs.aws.amazon.com/waf/latest/developerguide/logging.
- In the Choose source and destination section.
- In the Source section, select Direct PUT.
- In the Destination section, select Amazon S3.
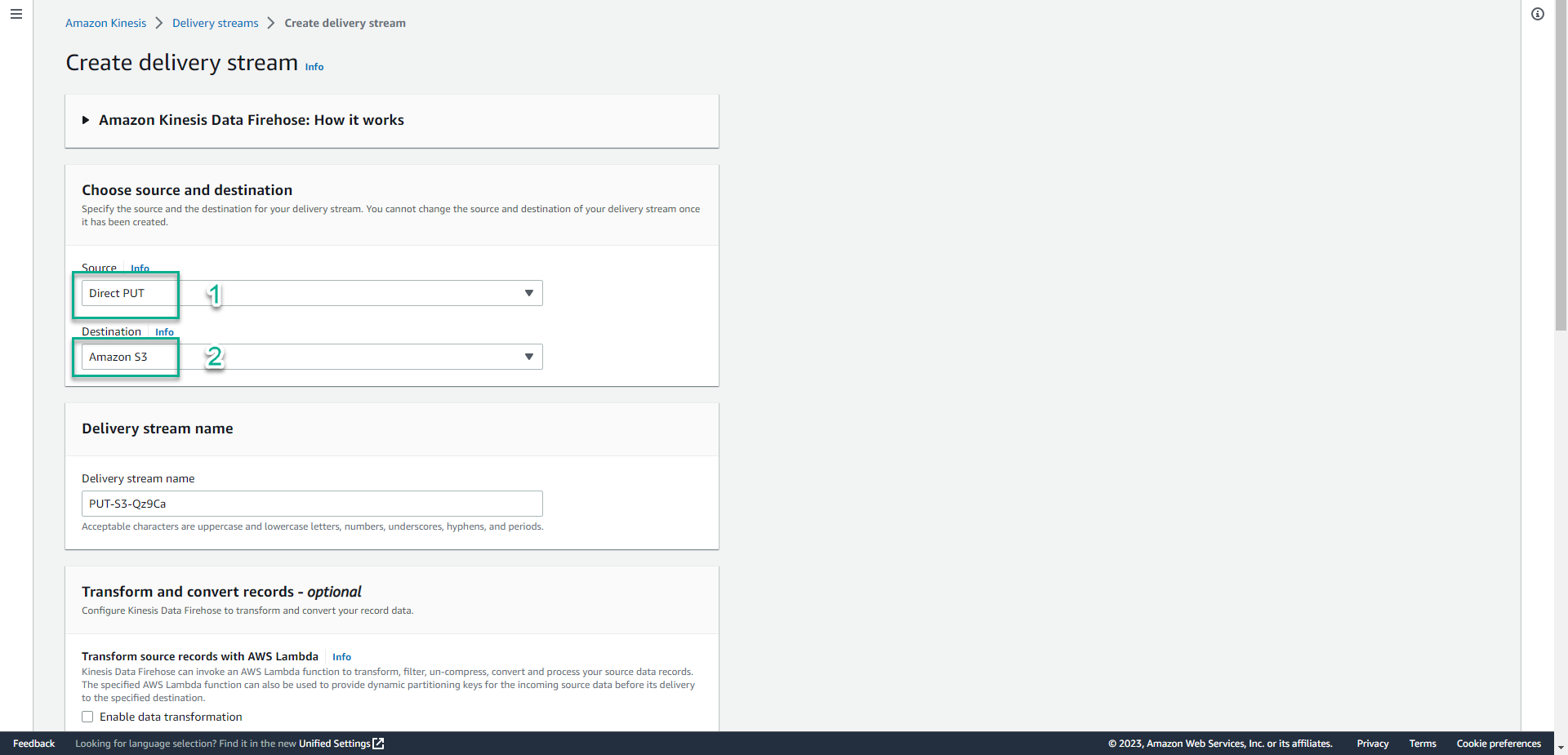
- In the Choose source and destination section, type
aws-waf-logs-workshop-26.Prefix the Kinesis Data Firehose with
aws-waf-logs-workshop-. This is required by the WAF service.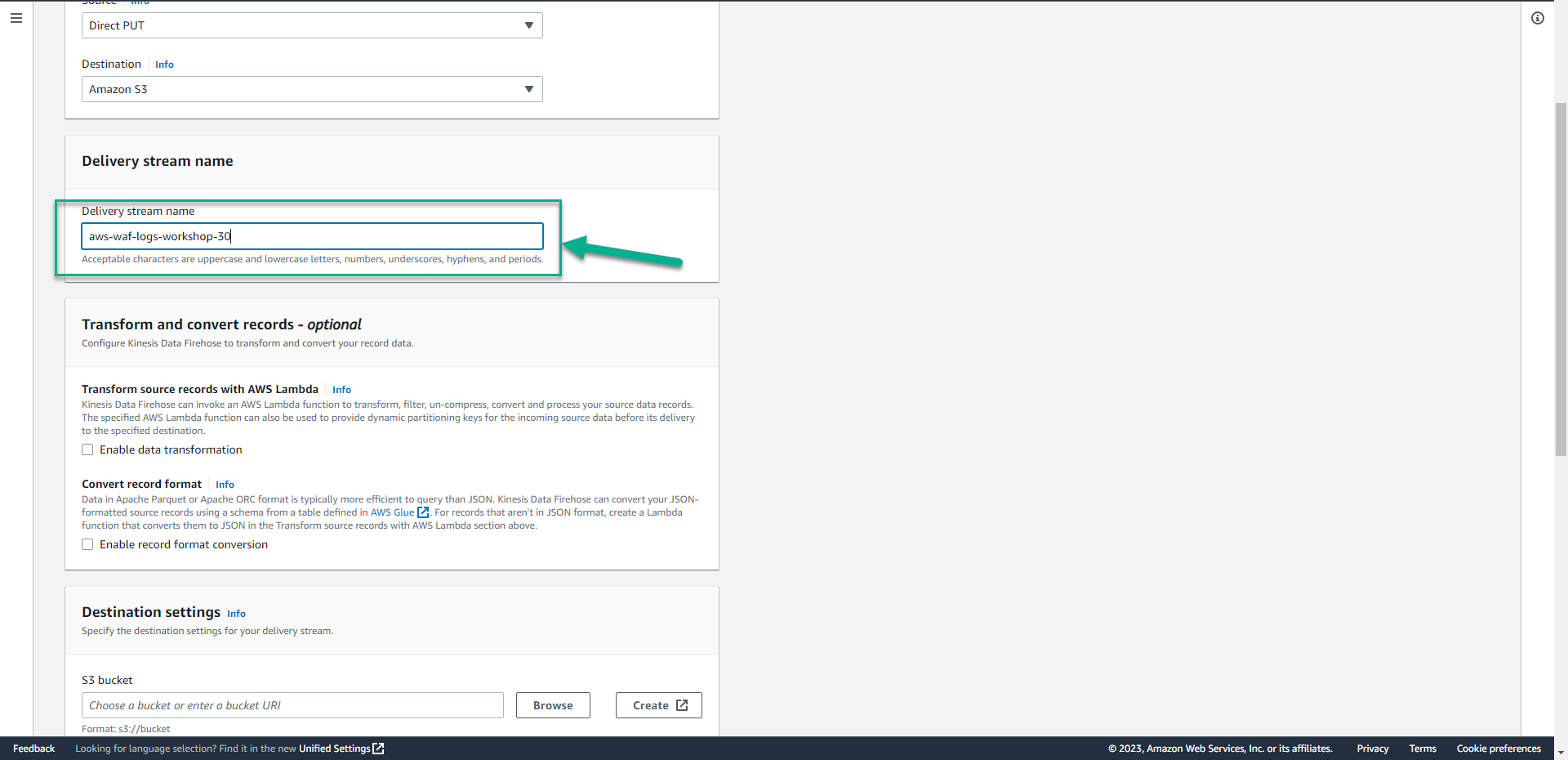
- In the Destination settings section.
- Click Browse.
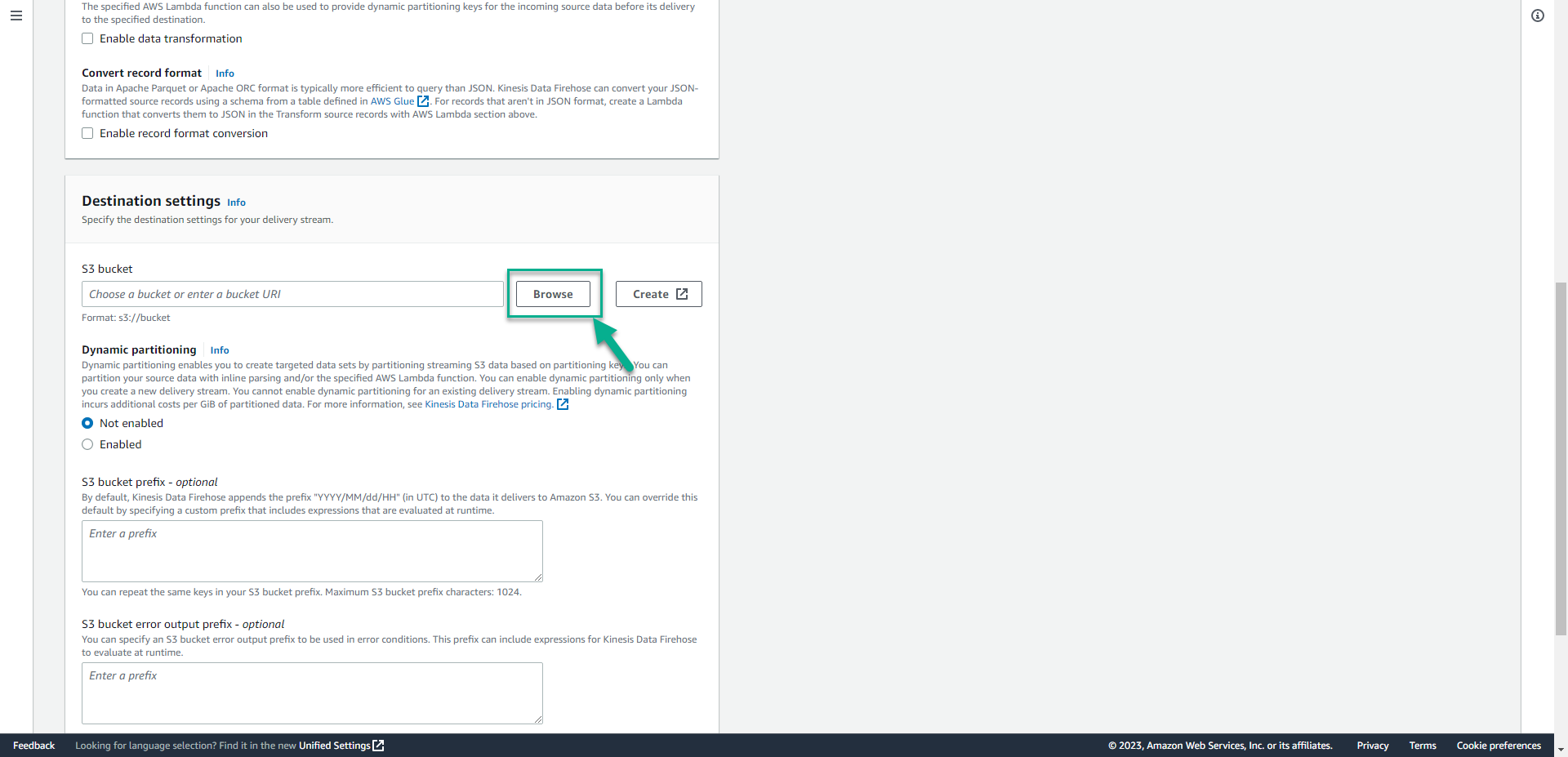
- Select aws-waf-logs-001(S3 bucket we created) is the storage.
- Click Choose.
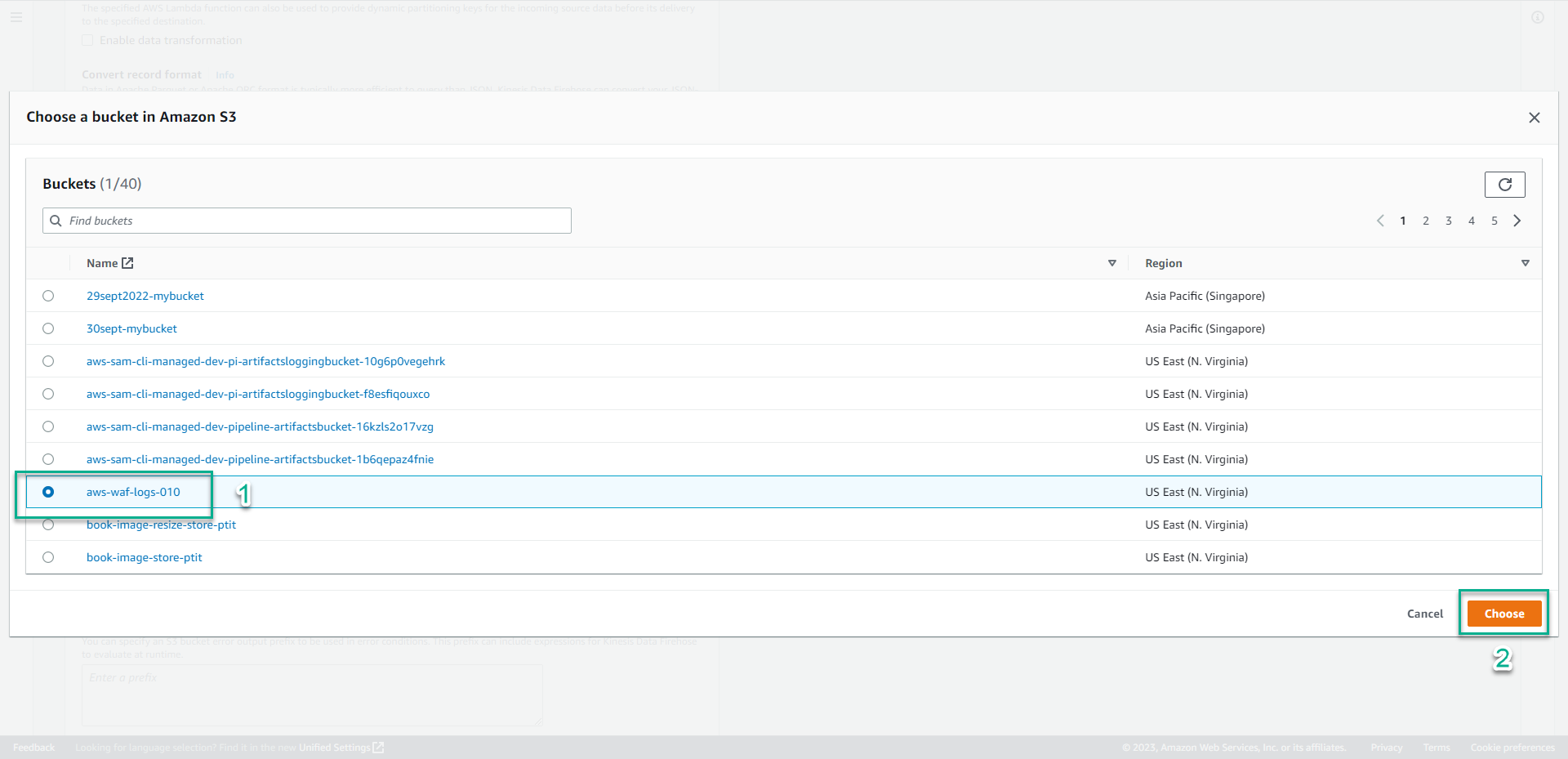
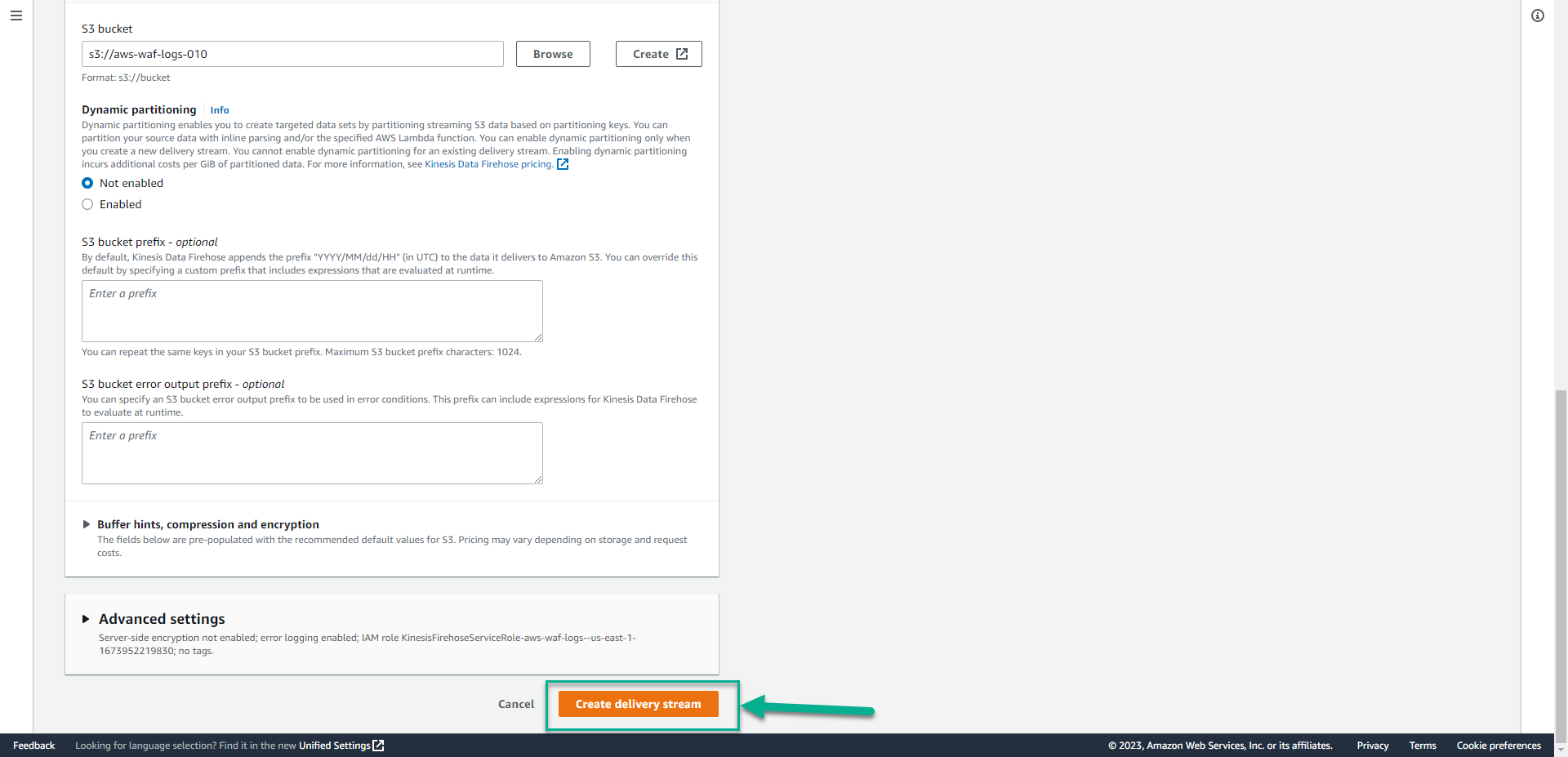
- Drag the screen down, Click Create delivery stream.
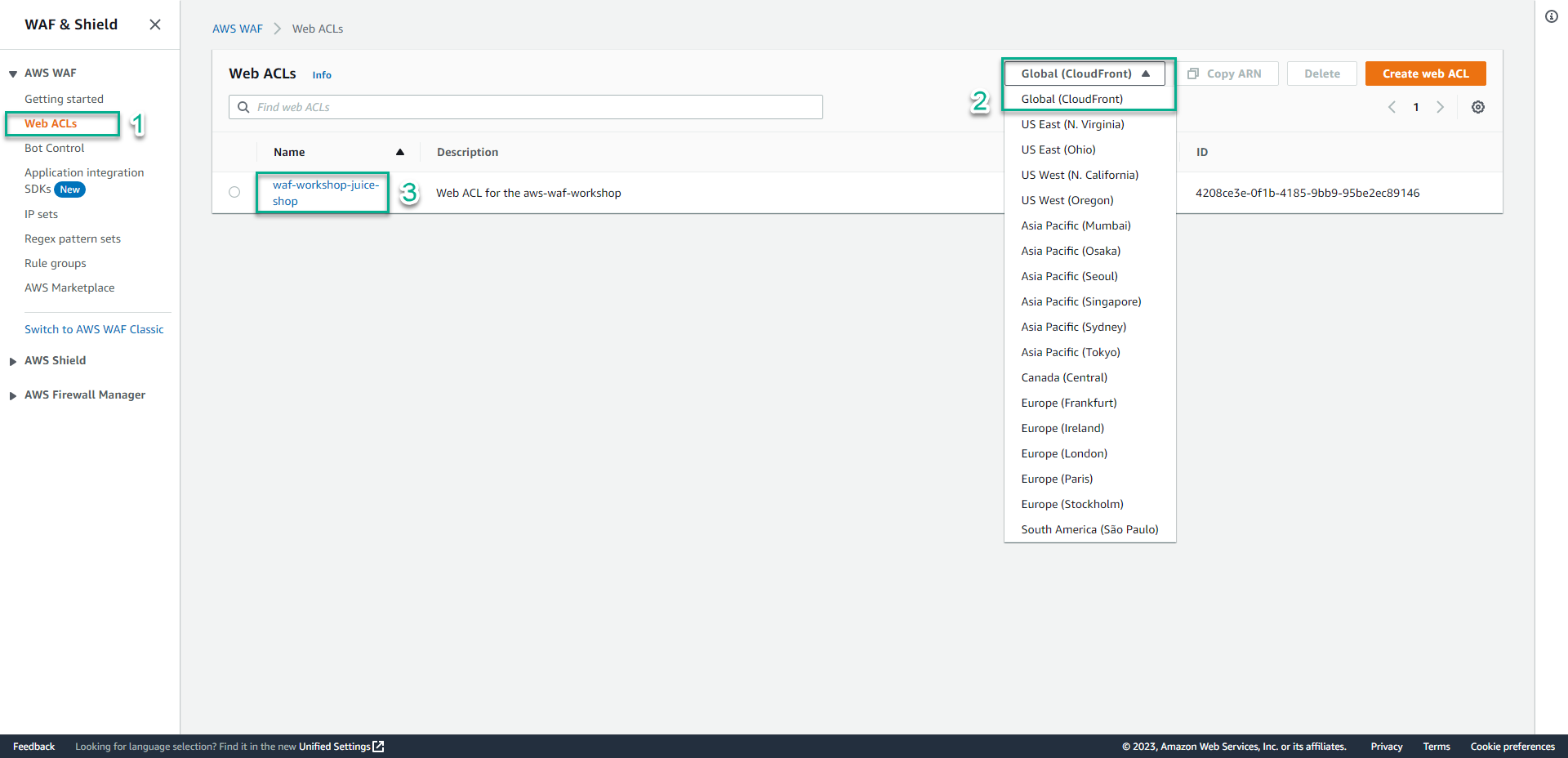
- Go to AWS WAF Console.
- Click Web ACLs.
- Select Global.
- Click waf-workshop-juice-shop.
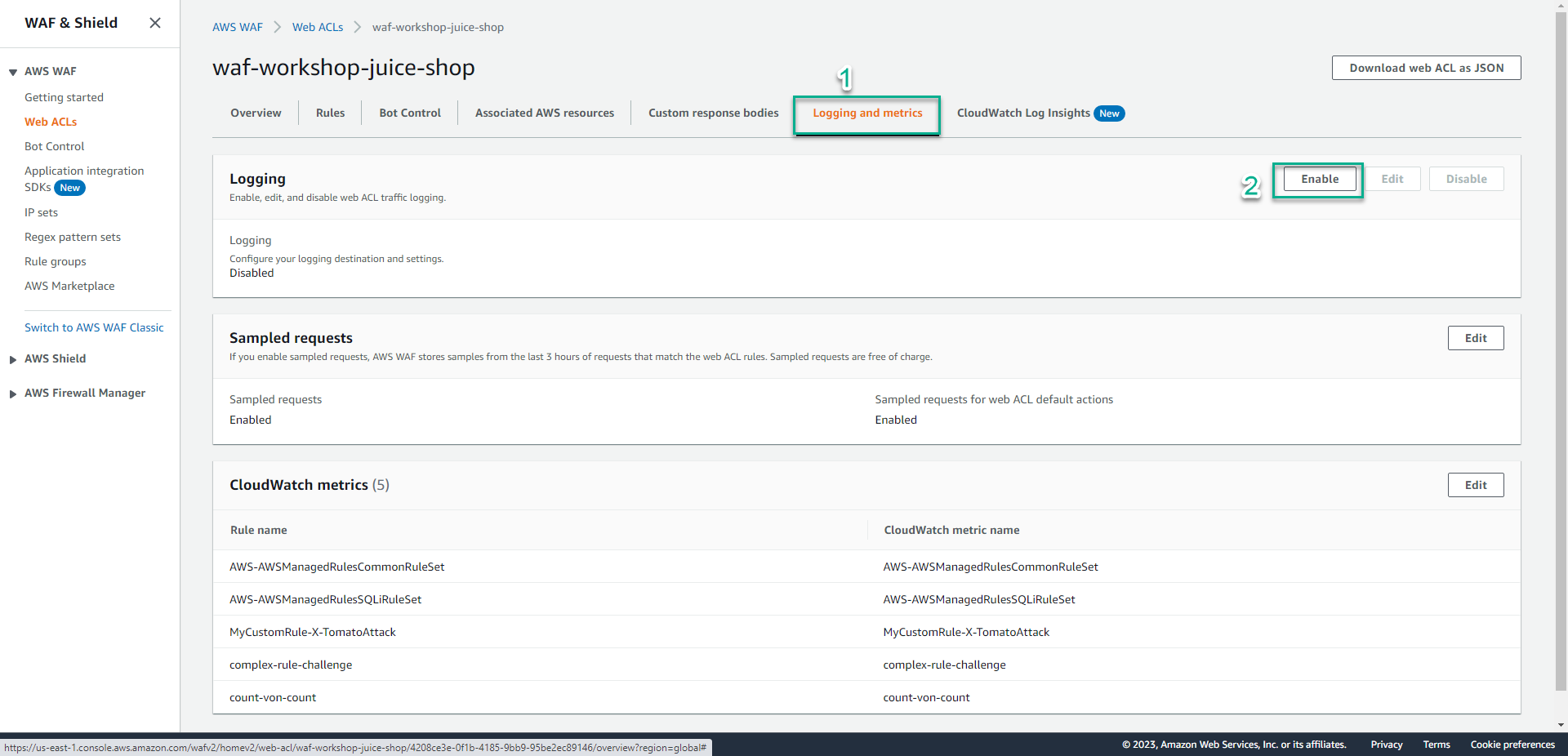
- In the information of your Web ACL page.
- Select Logging and metrics tab.
- Click Enable.
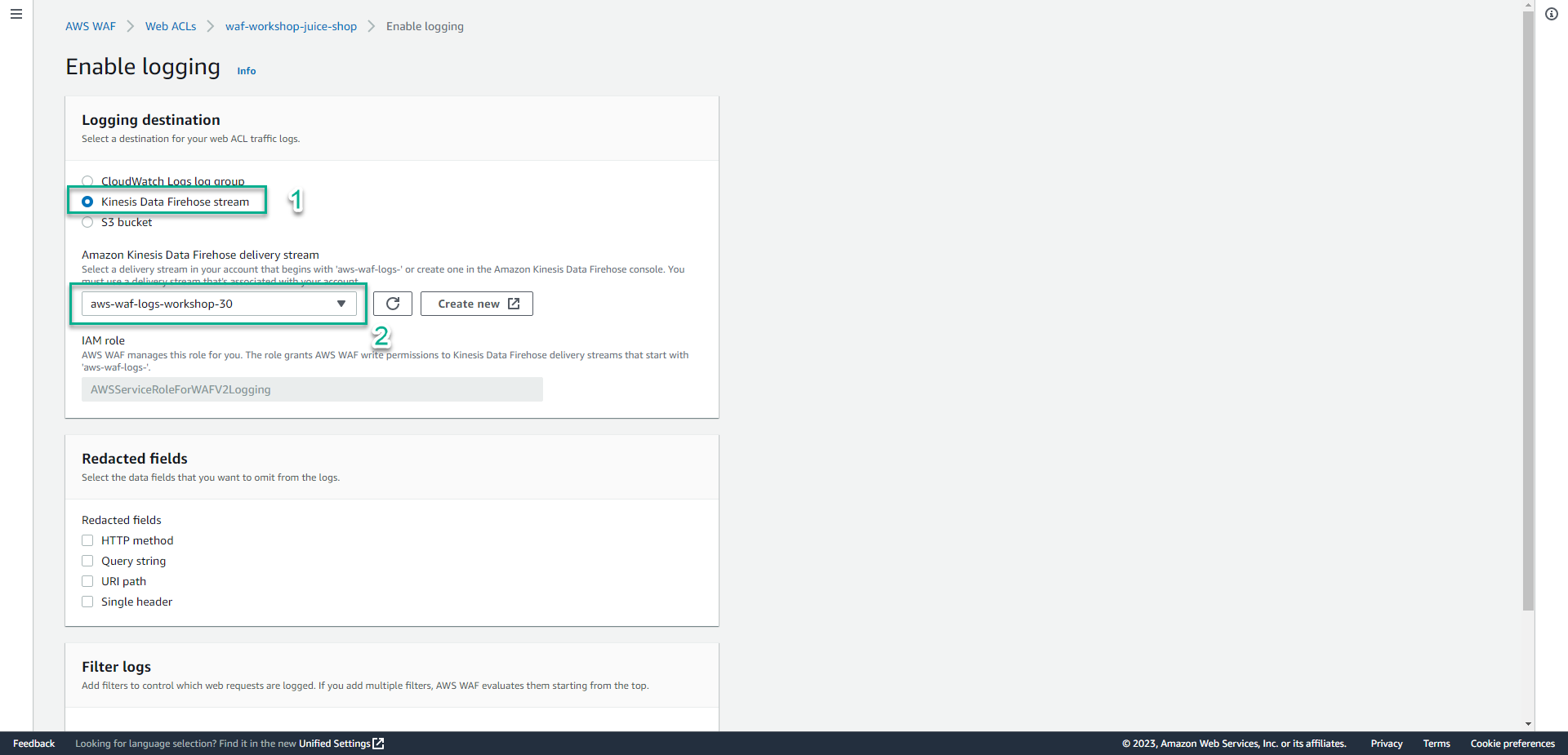
- In the Logging destination section.
- Click Kinesis Data Firehose stream.
- In the Amazon Kinesis Data Firehose delivery stream section, Select aws-waf-logs-workshop-26.
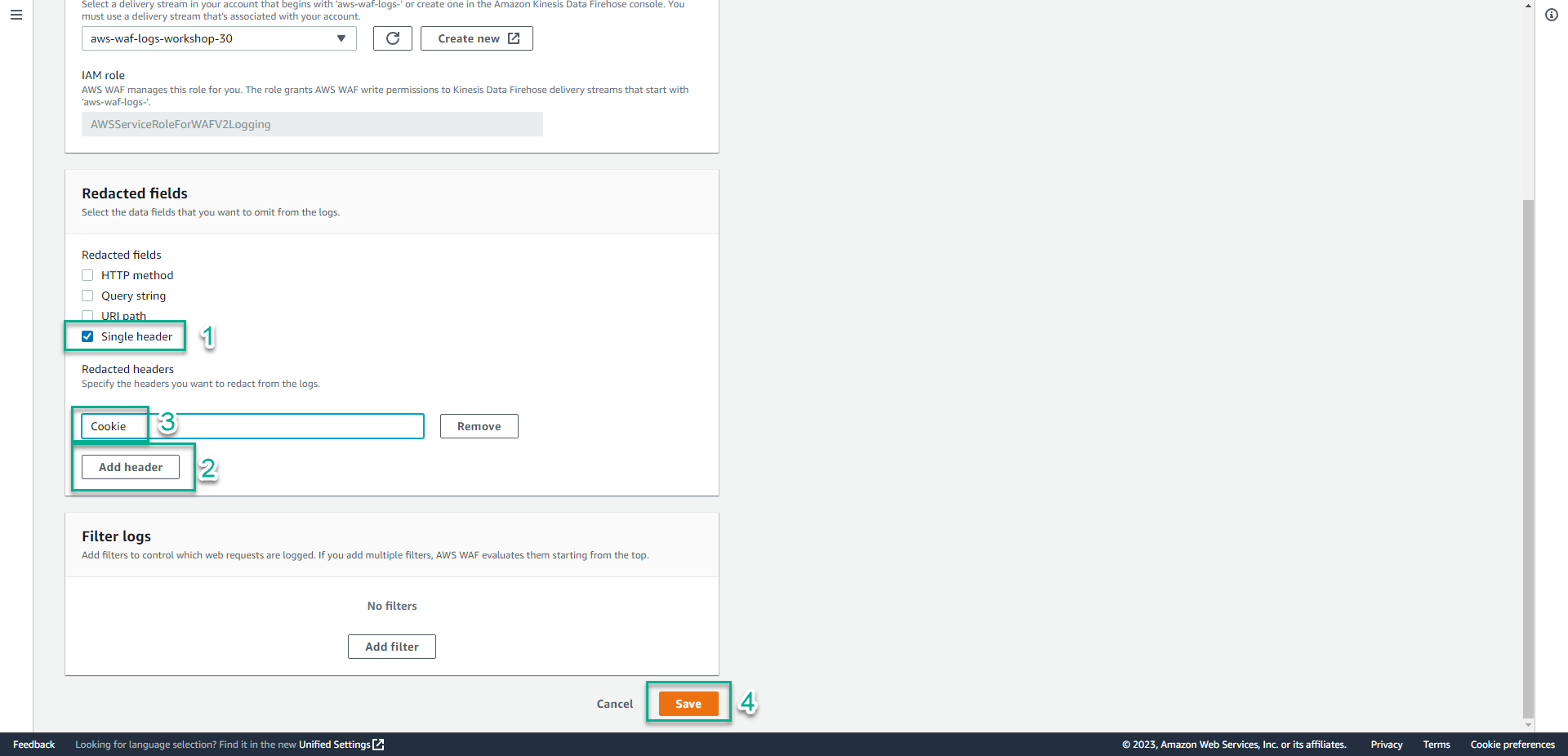
- In the Redacted fields section.
- Select Single header.
- In the Redacted headers section, Click Add header
- Add the header value:
Cookie. - Click Save
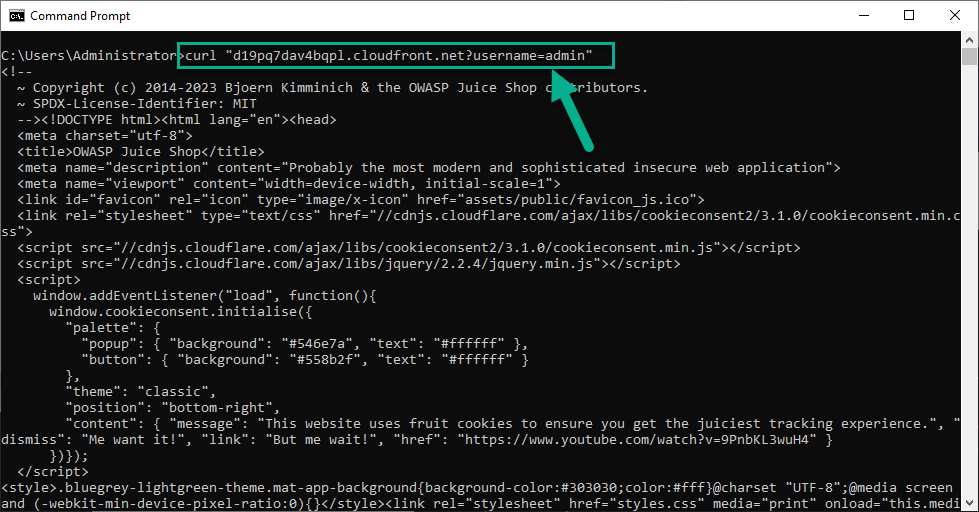
- Run command
curl "<Your Juice Shop URL>?username=admin"
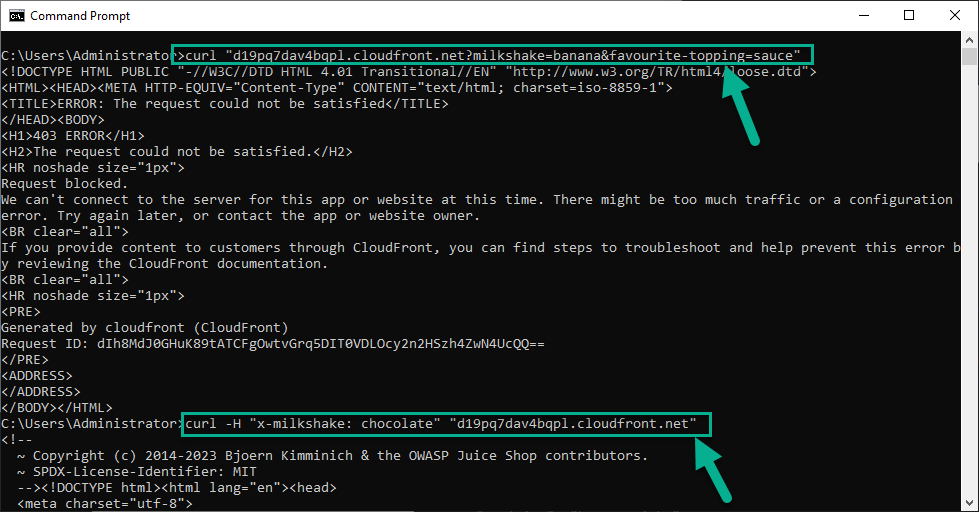
curl "<Your Juice Shop URL>?milkshake=banana&favourite-topping=sauce"
curl -H "x-milkshake: chocolate" "<Your Juice Shop URL>"
 11. Download the logged file in S3 bucket.
11. Download the logged file in S3 bucket.
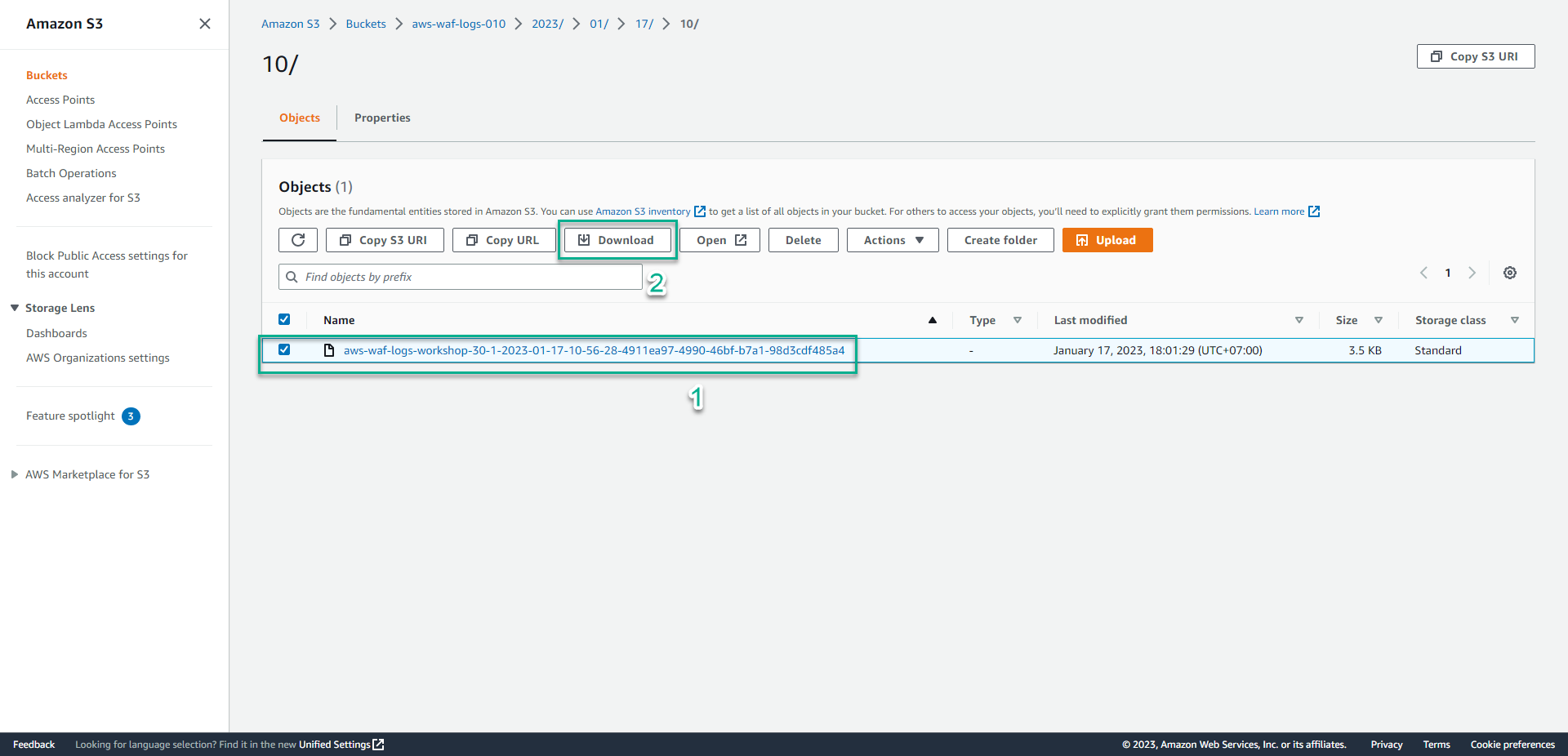 12. Search for the Cookie header in the logged file.
12. Search for the Cookie header in the logged file.
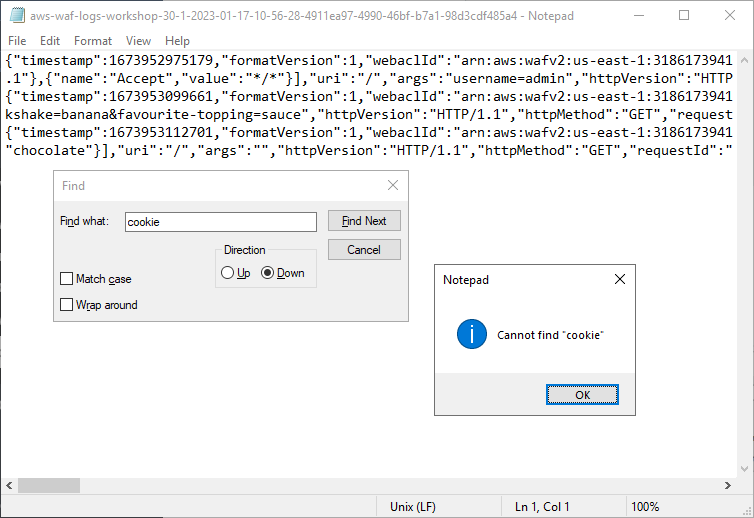
Conclusion
WAF allows you to capture request logs and store them in any Kinesis Data Firehose destination. The logs provide information of the request. The logs also provide the action and rule involved for a request. This information can be invaluable when running a WAF. Use field redaction to avoid logging sensitive information.